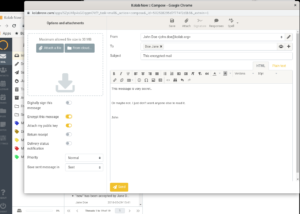
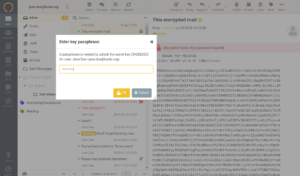
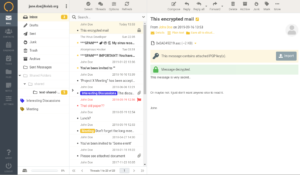
As mentioned in other articles in this knowledge base, Kolab Now has configured Perfect Forward Secrecy (PFS), data in transport is encrypted with SSL/TLS, and all systems are HMS encrypted. The web client provides the option of encrypting emails through PGP asymmetric keys . As other similar solutions, e.g. the use of browser add-ons like Mailvelope, the webclient is letting the server hold a copy of the public / private keys, which brings another level of security considerations into play. Providing true end-to-end encryption can only really be achieved by client encryption.
The use of encryption must come with a warning. There are many potential problems that users can get into with encryption keys. Let’s face it: PGP encryption is not the most user friendly technology the internet has seen ever.
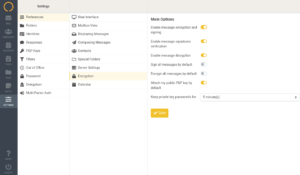
Our implementation of PGP encryption in the webclient is created to be as user-friendly as possible. It is guiding the user as well as possible through the curves and wiggles. A more detailed explanation of PGP can be found here.. or here.. This article, however, is about how to use the PGP implementation in the Kolab Now webclient.
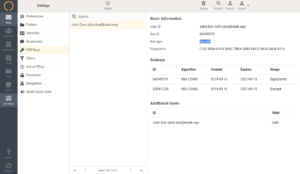
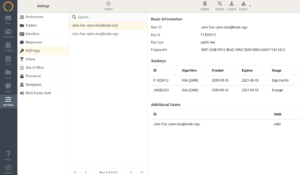
In short, PGP encryption is building on the premises that a user has a public and a private key. The public key is public, and can be distributed to anyone who is expected to encrypt messages, and the private key is private. It should never get distributed to anyone else.
To use the encryption functionality, one must first have a PGP private and public key. To avoid known security issues, users will have to create and publish their own keys. More information about how to do so can be found in one of these places:
- GnuPG Documentation
- PGP key pair creation on Linux (fedora)
- PGP key pair creation on Windows
- PGP key pair creation on Mac OS
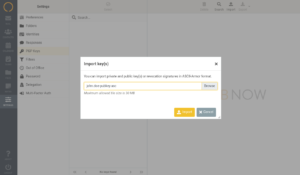
When the PGP key pair is available, the private key and the public key should be available as files. e.g. jdoe-privkey.asc / john.doe.pubkey.asc or john.doe.private.key.pgp / john.doe.public.key.pgp.
MAKE SURE TO BACK UP THESE KEY FILES AND STORE THE BACKUP IN A SAFE PLACE!!!
Please Note: According to the ToS, Kolab Now is not responsible for the encryption keys. It is up to the user to maintain those with regards to validity, publishing to key servers, revocation, ETC. Always make sure to save a backup of public and private keys in a safe place away from network connections (e.g. a USB key). This is valid for encryption keys, as well as for any other data.